
Blog
How to do Vulnerability Prioritization
A helpful guide to help teams understand what goes into choosing what to fix and when

Blog
A helpful guide to help teams understand what goes into choosing what to fix and when
Technical Guides
Explaining the use cases and how to implement an under-discussed Kubernetes feature
Product Reviews
Answering my most received question from the last 2 weeks

Resources and analysis on the latest zero days: CVE-2024-47176, CVE-2024-47076, CVE-2024-47175, and CVE-2024-47177
A small step towards total market coverage
A three part series detailing what data is helpful for operationalizing vulnerability management (1/3)

Technical Guides
A guide into understanding what reachability is
Walking through the process of fixing container vulnerabilities
And other realities from last week's fundraising
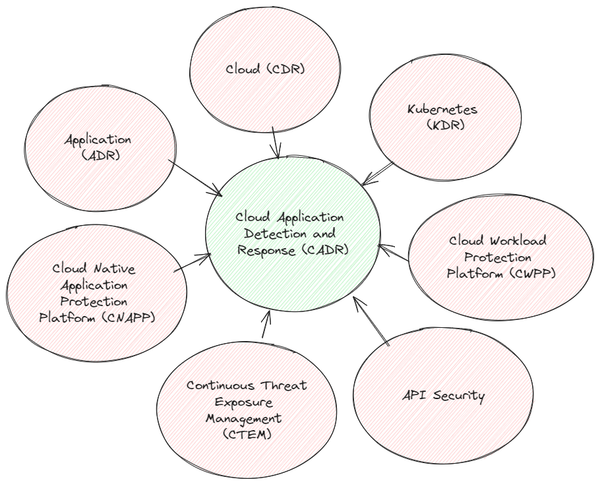
Everything security teams need to detect real time attacks against modern infrastructure (Part 3/3)
Exploring why many CNAPPs have a Kubernetes gap

TL;DR: Qualys research team discovered an issue where you can exploit OpenSSH with a “brute force” like timing attack from the outside. This will effect vulnerable OpenSSH library versions, which is essentially any public facing Linux server open on port 22. In my opinion, the likelihood on a real