Understanding the Polyfill Attack (Polykill)
And some thoughts about what it shows about our tooling trends
And some thoughts about what it shows about our tooling trends
Arguing for three pillars of runtime application visibility (2/3)

Let me cook, we're making the future here! Part 1/3.
Threat Model -> Design -> Scan -> Scale
No buzzwords or Gartner categories, just really important security stuff
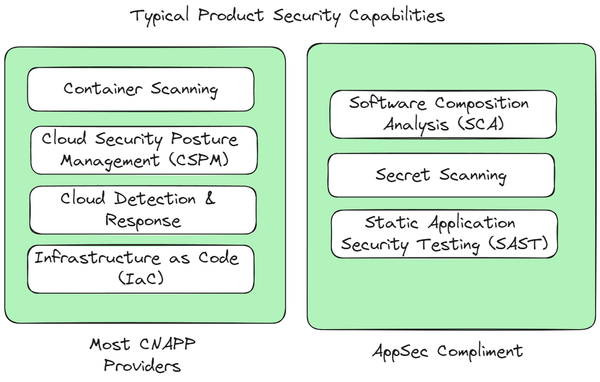
Despite what they'd tell you, CNAPP's don't do everything
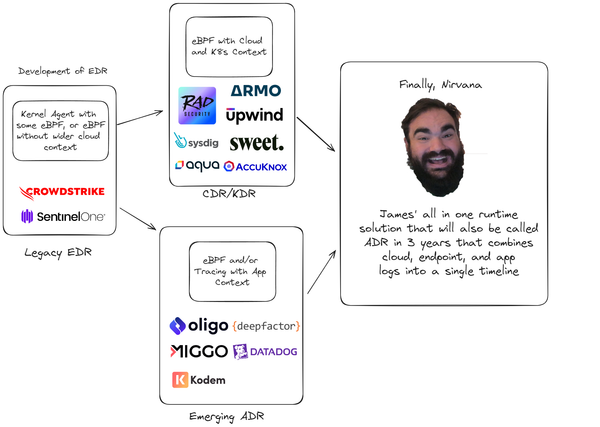
Application Detection Response is the hot off the press buzzword that's going to be the next big thing
RSA Takeaways Me and Jacob - Certified Sales Wiz at Opus A coworker told me “RSA is a marketing conference” and they couldn’t be more correct. I spent most of the time running from coffee shop to coffee shop, because most of my favorite vendors didn’t think spending
The best part of working on Latio is getting to see the amazing innovation across emerging security products. I was excited to see that this year I agree with most of the RSA Innovation Sandbox choices. I wanted to take this week to highlight some of their amazing work and
Platforms vs. Point Solutions Founded Dates of CNAPP Providers One recurring discussion in cybersecurity is the relative value of platforms versus point solutions. Conveniently enough, every platform provider thinks platforms are what the people really want; conversely, every point solution thinks platforms are an awful value proposition. The truth lays
The Heart of Reachability A while ago, I wrote an article called “5 types of reachability analysis” with Endor Labs. In that article, I talked about the 5 types of reachability, which I summarized as: * Function-level reachability * Package baselining * Internet reachability * Dependency-level reachability * Package used in image At the heart
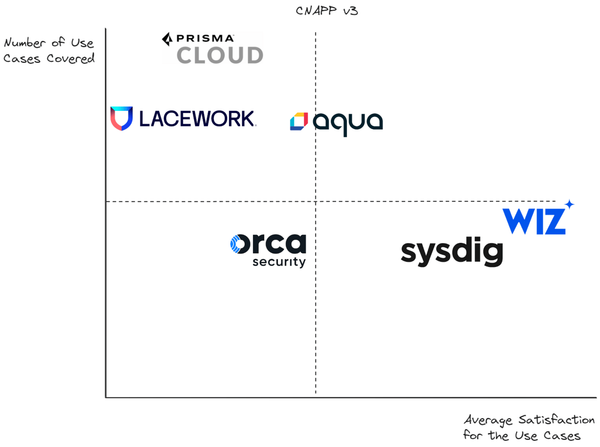
Death to CNAPP!