Qix NPM Supply Chain Attack: What Teams Need to Know
Responder Resources

Latest Updates
- Another package from a different maintainer has been impacted: proto-tinker-wc@0.1.87
- Malcious package versions have been removed from NPM
- You would be impacted if you deployed any of these malicious package versions the morning of September 8th (EST). The impact is users visiting your website under specific circumstances having crypto stolen.
- The attacker has reported to NPM, and their co-maintainer is removing the affected malicious versions they have access to; however, not all malicious packages have been removed.
- The attack, at this time, does not appear to have run anything locally, it was replacing crypto wallet IDs with the attacker's wallet when a user visited an infected website in several different ways
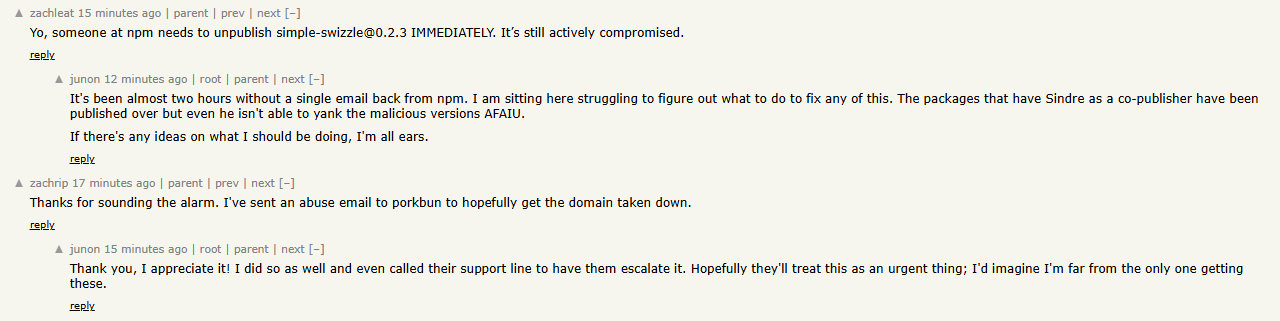
Maintainer is waiting NPM for takedown on the malicious package still up (simple-swizzle 0.2.3), and DNS provider for the phishing domain (npmjs[.]help)
What Happened
On Monday September 8, 2025 at approximately 10:30am EST Aikido Security discovered an ongoing compromise of the open source maintainer Qix's NPM account. The impacted repos have millions of downloads per week and should be assumed compromised. This situation is still unfolding, we'll be keeping this page up to date with available resources given this is a popular and widely used NPM package.
It appears that the NPM credentials of popular maintainer Qix were compromised via phishing and malicious code published to 18 of the maintainer's repositories. This code is still being analyzed, but seems to focus on stealing crypto information from end users when these packages are used on frontends. These packages are extremely common, especially as transitive dependencies.
Helpful Links
Aikido Article
Aikido LinkedIn post
Hackernews
Maintainer Bluesky
Main GitHub Issue
Deobfuscated Attack Code
Attack Breakdown Substack
Handy Commands
Check for Malware in your dependency tree with ripgrep (run this in the folder that has node modules in it):
brew install rg
rg -u --max-columns=80 _0x112fa8
NPM List effected packages:npm list backslash chalk-template supports-hyperlinks has-ansi simple-swizzle color-string error-ex color-name is-arrayish slice-ansi color-convert wrap-ansi ansi-regex supports-color strip-ansi chalk debug ansi-styles proto-tinker-wc
IoCs:
Attacker Crypto Wallets: https://gist.github.com/jdstaerk/f845fbc1babad2b2c5af93916dd7e9fb
Phishing domain (now taken down): npmjs[.]help
Packages Effected
| Package / Component | GitHub Link | Version |
|---|---|---|
| backslash | Link | 0.2.1 |
| chalk-template | Link | 1.1.1 |
| supports-hyperlinks | Link | 4.1.1 |
| has-ansi | Link | 6.0.1 |
| simple-swizzle | Link | 0.2.3 |
| color-string | Link | 2.1.1 |
| error-ex | Link | 1.3.3 |
| color-name | Link | 2.0.1 |
| is-arrayish | Link | 0.3.3 |
| slice-ansi | Link | 7.1.1 |
| color-convert | Link | 3.1.1 |
| wrap-ansi | Link | 9.0.1 |
| ansi-regex | Link | 6.2.1 |
| supports-color | Link | 10.2.1 |
| strip-ansi | Link | 7.1.1 |
| chalk | Link | 5.6.1 |
| debug | Link | 4.4.2 |
| ansi-styles | Link | 6.2.2 |
Shout out to the Aikido team for not only finding this vulnerability but for disclosing it quickly for teams to take action. I've added their breakdowns, announcements of what happened.
Commentary
- We really need CI flags for malware versus vulnerabilities, as many teams would want to block on one but not the other - including for
npm audit - NPM install wrappers would stop this, but only once detected as malware, and adoption rates tend to be really low
- Aikido's AI malware detection caught this really quickly